How to Audit Passwords
If one member of your team uses a weak password, it exposes your entire network to threats. Likewise, if one member of your team reuses their strong password elsewhere and it is pwned, then your entire network is exposed.
Passwords have become the main point of entry for hackers. Any password complex enough to garner security cannot be remembered easily, and with an ever-increasing number of passwords being needed, users often reuse them, which is a huge security risk.
Between weak and reused passwords, your network is far less secure than it would be by design. The first step in rectifying this situation is to audit passwords on your network.
Table of Contents
What is a Password Audit?
A password audit is a systematic review of the passwords used within your network to identify security weaknesses. By leveraging specialized software, the audit simulates various attack methods, such as dictionary attacks and brute force attacks, similar to those employed by hackers.
The purpose of a password audit is to pinpoint vulnerabilities like weak or compromised passwords, reused credentials, and other security gaps. The software scans for these issues by attempting to break into your network, mimicking the techniques that malicious actors might use. By identifying and addressing these weaknesses, you can significantly enhance your network’s security and protect sensitive data from unauthorized access.
Why Audit Passwords?
The fact is that passwords are fatally flawed: they need to be complex and unique, they need to be different for each site, you need to remember them, and you shouldn’t store them somewhere unsafe like on a post-it note on your monitor or an Excel file. Human nature is hard to avoid, and it runs counter to the aim of secure passwords.
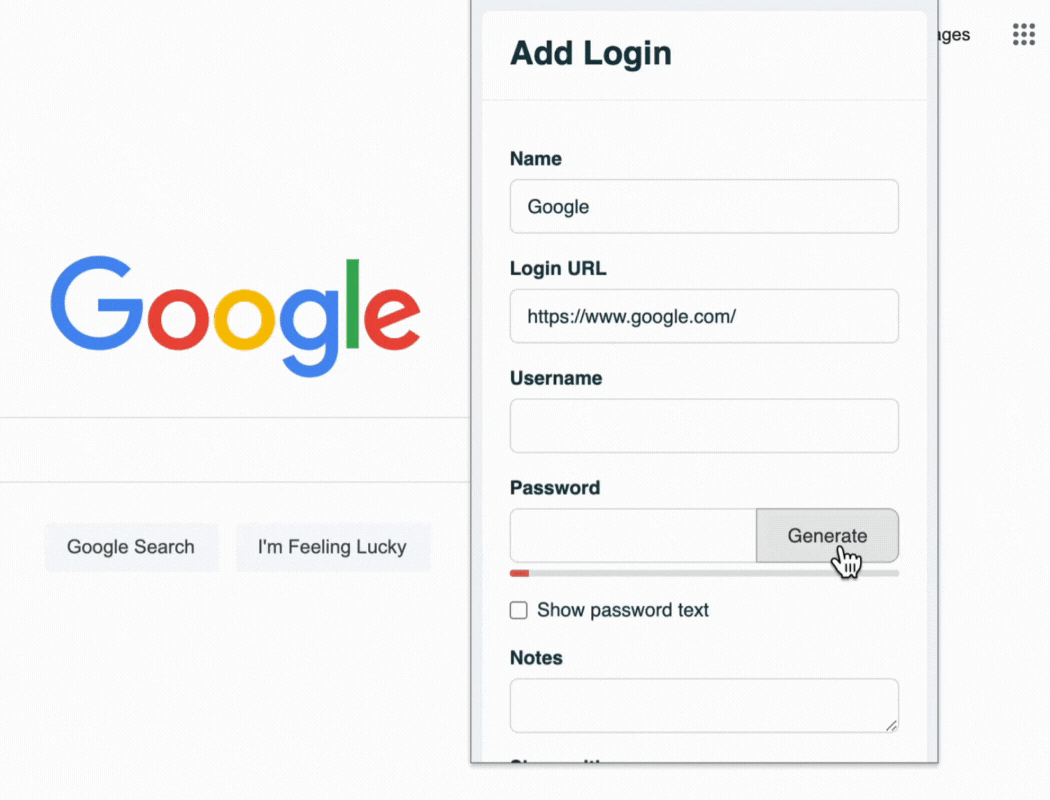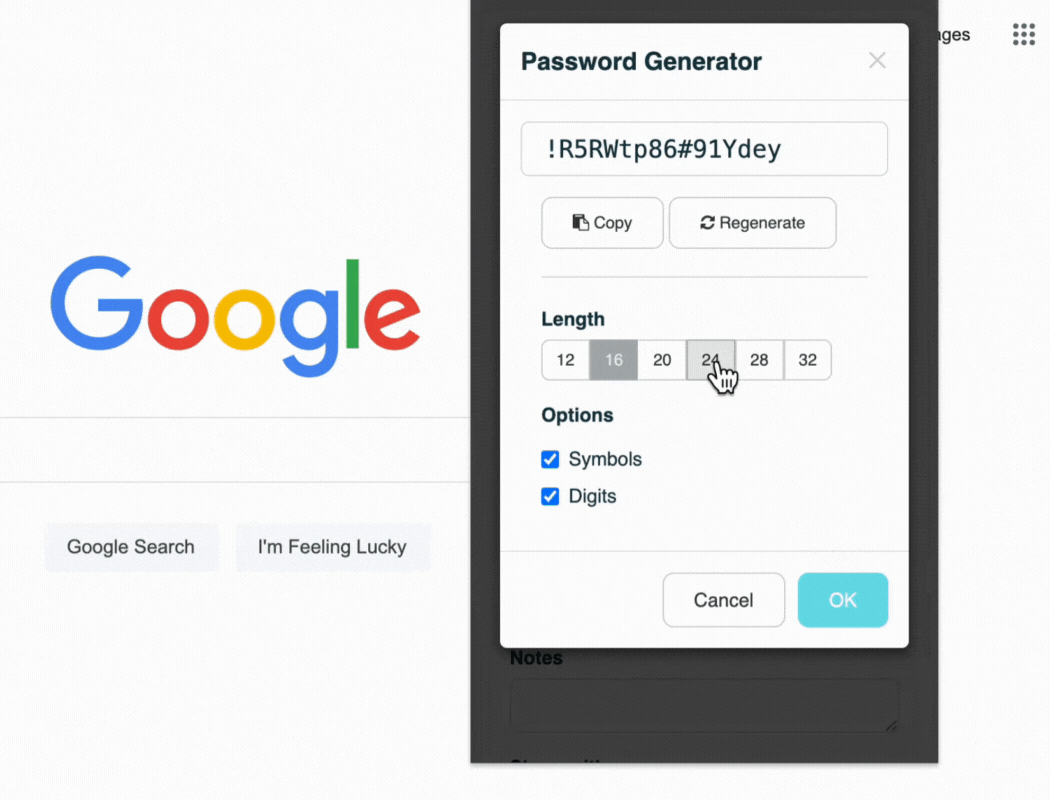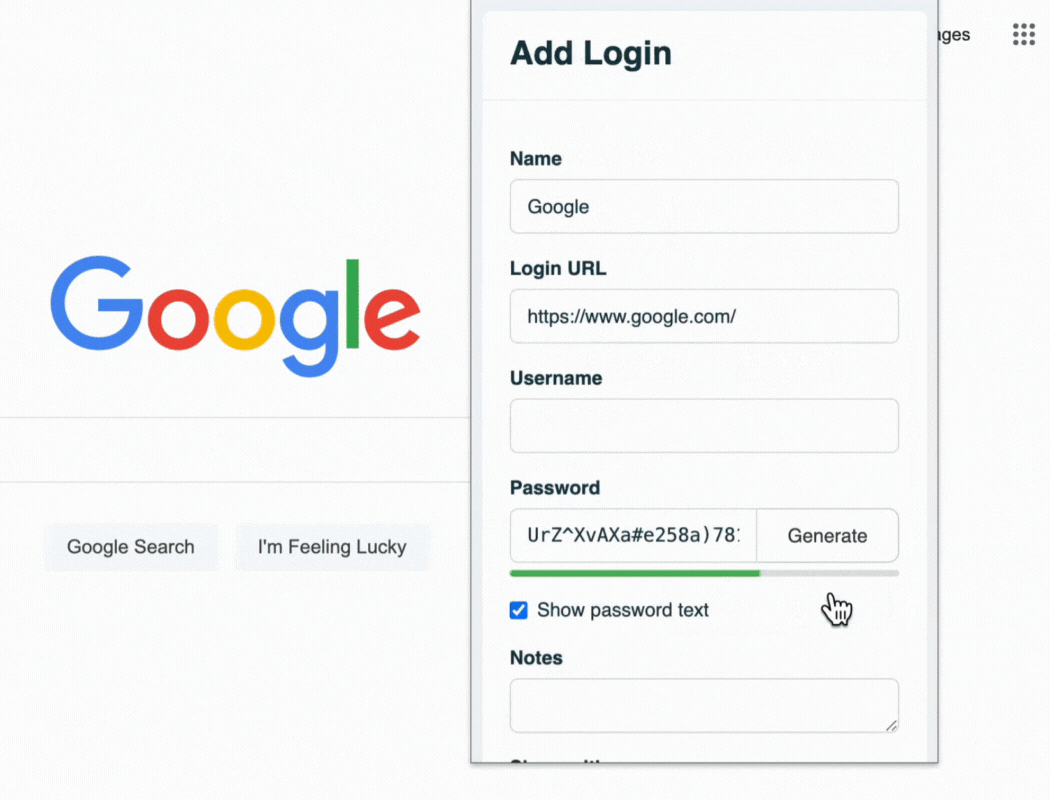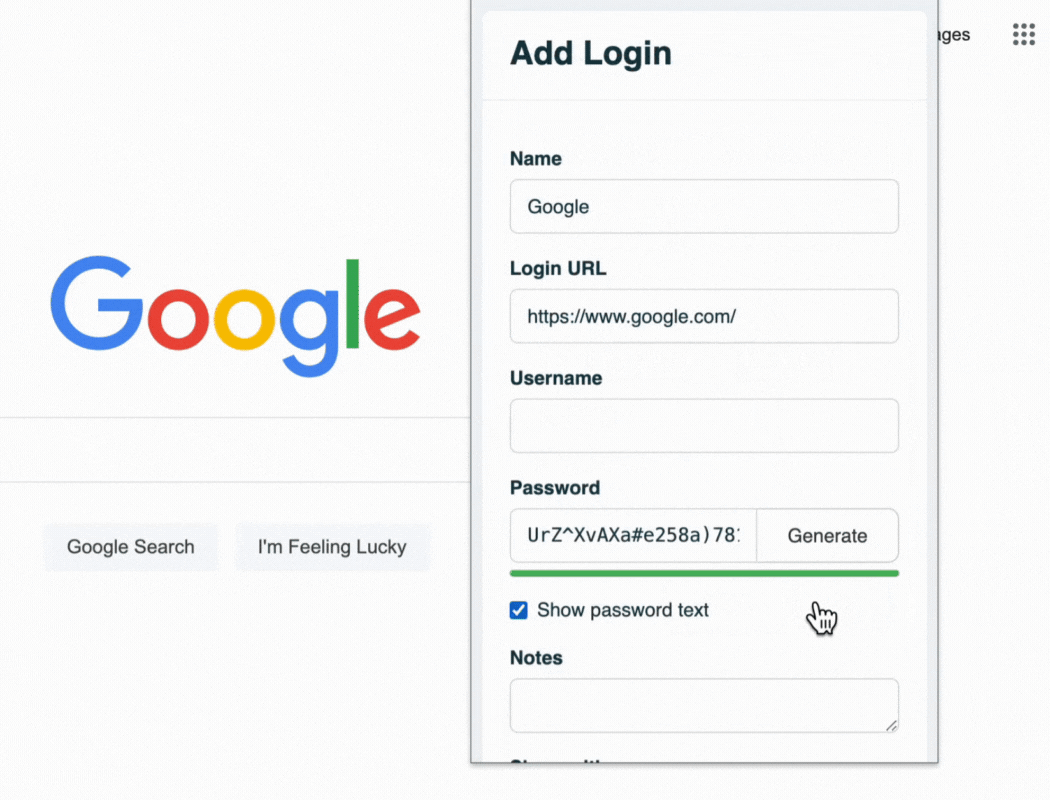
Use a password generator to test the strength of your password
Of course, a strong password manager helps, but before you get the most out of the added security and convenience of a password manager, you need to be confident that the passwords being used to access your network are secure.
Let’s assume everyone on your team understands that they shouldn’t reuse passwords and have chosen a unique one for their work login, as well as the logins for all the tools they use at work. That’s great.
Let’s assume you enforce password complexity to maximize security. That means everyone must choose a password with a minimum length of 12 characters and that it must have at least one each of lowercase letters, uppercase letters, numbers, and a set of characters. That is, it meets the following requirements:
- Lowercase letter {abcdefghijklmnopqrstuvwxyz}
- Uppercase letter {ABCDEFGHIJKLMNOPQRSTUVWXYZ}
- Number {0123456789}
- Character {!@#$%^&*()_+{}|:"<>?~`-=[]\;',./}
That’s great, too. But, is it enough? Well, to crack that password by trying 20,000,000,000 attempts per second, which is easily accomplished using a cloud computing platform, would take a maximum of approximately 6,600 years and an average of half that, or 3,300 years. Problem solved, right?
Well, it depends on what kind of passwords your team is choosing. If they are picking truly random passwords, then it is unlikely anyone will ever crack those codes. But there’s a difference between passwords that can be brute force attacked and those that are easy to guess. For example, “Password#333” matches the requirements but isn’t going to take any longer than “password” to guess.
To understand this fully, we need to understand the difference between a brute force attack and a dictionary attack. The brute force attack starts with “aaaaaaaaaaaa,” then “aaaaaaaaaaab,” and so on until the password is found.
A dictionary attack, conversely, tries every word in a dictionary. Although these dictionaries might include the entire Oxford English Dictionary, they go well beyond that and include the words commonly used as passwords and variations of those passwords. For example, in addition to “password,” they might include “p4ssw0rd”, “pa55word”, “passwordpassword,” etc.
Passwords need to be safe from both, and auditing passwords will tell you whether you have either issue.
Don't let your company fall victim to extortion emails, credential stuffing, or any other password vulnerability. Let TeamPassword take care of security while you focus on growing a successful business!
Sign up for a 14-day free trial to test TeamPassword with your team members today.
How do you Audit Passwords?
To audit passwords, you need to use specialized software. We provide a list of several popular tools to audit passwords in the following section. But how do they work?
Essentially, the password auditing tools attempt to guess the passwords being used on your network. They do this through a combination of dictionary and brute force attacks, among other attacks, and then notify you about any other ways that the passwords might be compromised, for example, by being pwned.
Once you have performed a password audit, you can then notify any users whose passwords have been compromised or too weak so that they can change them.
What are some tools to audit passwords?
You’ve decided to audit the passwords on your network, but what program should you use? Here are five popular password auditing apps.
RainbowCrack
RainbowCrack is based on Phillippe Oechslin’s faster time-memory trade-off technique. It is a brute force hash cracker that generates all possible plaintexts and then computes the corresponding hashes on the fly. Next, it compares the hashes to the one that needs to be cracked.
If a match has been found, then the plaintext has also been found. Conversely, if all possible plaintexts have been tested, but no match has been found, then the plaintext has not been found.
RainbowCrack requires a pre-computation stage that involves time-consuming computations.
Wfuzz
Wfuzz is another tool designed to brute force attack web applications. It was originally created to assess web applications, but it can also be used to find hidden resources, e.g., directories, servlets, and scripts.
Cain and Abel
Cain and Abel is a password recovery tool. It is available for Microsoft operating systems. It can help recover lost passwords by using several types of attacks. These include dictionary attacks, brute force attacks, and cryptanalysis attacks.
It can also decode scrambled passwords, record VoIP conversations, reveal password boxes, uncover cached passwords, recover wireless network keys, and analyze routing protocols.
Cain and Abel was originally developed for use by network administrators, teachers, security consultants, forensic investigators, network penetration testers, etc.
THC Hydra
THC Hydra is a common choice for performing brute force cracks of remote authentication services because it can perform quick dictionary attacks on more than 50 protocols, such as Telnet, FTP, HTTP, https, smb, and various databases.
THC Hydra is a fast network login password cracking tool. New modules can be installed easily to enhance its features. It is currently available for Windows, Linux, Free BSD, Solaris, and OS X.
Ncrack
Ncrack is another fast network authentication cracking tool. It was originally designed to help companies improve the security of their networks by testing their hosts and network devices for poor passwords.
Because Ncrack enables rapid, reliable, and large-scale password auditing, it is also used by security professionals. Furthermore, it has a flexible interface that gives the user full control of network operations.
The protocols supported include RDP, SSH, HTTP(S), SMB, POP3(S), VNC, FTP, SIP, Redis, PostgreSQL, MySQL, and Telnet.
What are common issues found when you audit passwords?
Weak Passwords
Weak passwords are often too short, too simple, or too common. These types of passwords are highly susceptible to various attacks:
-
Short passwords: Passwords with fewer characters are vulnerable to brute force attacks, where an attacker uses automated tools to test all possible combinations. Short passwords significantly reduce the total number of combinations that need to be tested, making them easier to crack.
-
Simple passwords: Using predictable sequences like "123456" or "password" makes passwords susceptible to easy guessing.
-
Common passwords: Passwords based on easily obtainable personal information, like your child’s name or birthdate, are particularly vulnerable to dictionary attacks, where attackers use lists of common passwords or personal data to guess the correct combination.
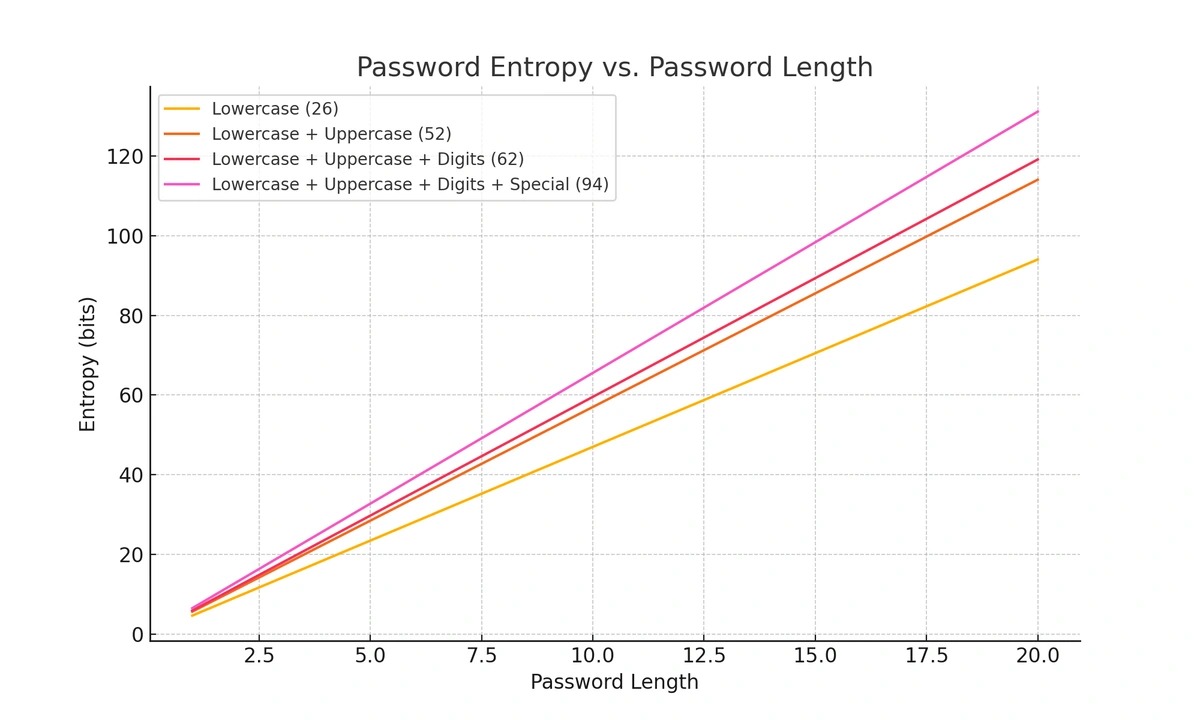
Password length greatly affects strength
Regardless of the type, weak passwords should be identified during an audit and changed immediately to stronger, more secure ones.
Compromised Passwords
A “pwned” password is one that has been exposed in a data breach. When a username and password combination is leaked online, hackers add those credentials to their databases and attempt to use them on other accounts, exploiting the fact that many users reuse the same passwords across multiple services.
Because password reuse is so common, pwned passwords often appear in password audits. These passwords should be changed immediately. You can check if your credentials have been compromised using tools like Have I Been Pwned.
Identical Passwords
Reusing passwords across multiple accounts can have catastrophic consequences. Once a hacker obtains one password, they can use it to try and access other accounts tied to the same user. This practice, called credential stuffing, is highly effective. Therefore, it is critical to ensure that each password is unique across all accounts.
Expired Passwords
Depending on the security protocols in place, some passwords may have expiration dates. A good audit will identify not only passwords that are already expired but also those that are about to expire. These should be changed promptly to maintain the integrity of your system's security.
Whatever issues are found during your password audit, the best thing you can do to prevent further issues is to help your users create strong passwords by providing a password manager. TeamPassword is the best way to make your team proactive participants in network security.
Your password manager should have secure sharing and fluid organization so that you can adhere to the principle of least privilege (PoLP). TeamPassword offers unlimited groups, AES 256-bit vault encryption, and two-factor authentication so you have peace of mind.
Before anyone can access the list of shared passwords, they must log in to the platform using their personal password and, should you choose to enforce multi-factor authentication (which we recommend), a short-term authentication code.
Teams often need to share passwords to access mutual accounts, but you don't have to put your data at risk to make this possible. Instead, use TeamPassword to securely generate, store, and share passwords within a team.
Sign up for a 14-day free trial to test TeamPassword with your team members today.